What Is Honeypots Crypto Scam? How Does It Improve Network Security?
0
0

Honeypots are a type of security mechanism designed to deceive attackers by creating a virtual trap. This involves intentionally creating a vulnerable computer system that attackers can exploit. It is important to have a good understanding of honeypots to improve security policies. Honeypots can be used on various resources including software, file servers, routers, and more.
Honeypot are a form of deception technology that help to identify the behavioral patterns of attackers. Security teams often use honeypot to investigate cybersecurity breaches and gather intelligence on cybercriminal operations. By using honeypots, the risk of false positives can be reduced when compared to other cybersecurity measures.
Honeypot are smart contracts that appear to contain a design flaw that enables any user to drain the contract’s Ether (Ethereum’s native currency) by sending a specific amount of Ether to the contract in advance. But, when the user tries to take advantage of this apparent bug, a second, unidentified trapdoor appears, preventing the ether draining from being successful. Now tell me what a honeypot does.
The intention is for the user to overlook any indications that the contract contains a second vulnerability in favor of concentrating solely on the obvious problem. Similar to other forms of fraud, honeypot assaults work because people are commonly susceptible to deception. As a result, people’s greed and presumptions frequently prevent them from accurately estimating risk.
Type of Honeypot Deployment
There are three different types of honeypot deployment methods available: pure honeypot, low-interaction honeypots, and high-interaction honeypots. Each of these methods serves a specific purpose in detecting and preventing cyber-attacks.
Pure honeypot: are designed to replicate an entire production system and are very basic in nature. When an attack occurs, it will be redirected to the honeypot. These honeypots are not very sophisticated and are mainly used for research purposes.
Low-interaction honeypot: imitate services and systems that attract the attention of cybercriminals. The honeypot collects data from blind attackers such as worms, malware, and botnets. These honeypots are more effective than pure honeypots and are less complex.
High-interaction honeypot: are complex setups that look like real production infrastructure. These honeypots do not restrict the activity level of attackers, which provides a more extensive cybersecurity solution. However, they require higher maintenance and expertise, including virtual machines. The purpose of high-interaction honeypots is to prevent attackers from accessing the real system.
It is important to choose the right honeypot deployment method based on the organization’s cybersecurity needs. Pure honeypots are useful for research purposes, while low-interaction honeypots are more effective in detecting and preventing attacks. High-interaction honeypots provide the most extensive cybersecurity, but they require more maintenance and expertise. Overall, honeypots are a valuable tool for detecting and preventing cyber-attacks.
Honeypots Used for?
The implementation of honeypots is a useful strategy for capturing unauthorized access attempts and identifying potential cyber attackers. Honeypots simulate legitimate parts of a network and attract intruders who believe they are accessing real systems. This allows security teams to gather information about attackers and study their behavior.
One way to enhance honeypot is by using spam traps. Spam traps are designed to attract web traffic to email addresses and can be used in conjunction with honeypots. Project Honey Pot is an example of a service that embeds spam traps into website software to collect information on spammers, including IP addresses, email addresses, and other site addresses.
Spam traps are not a security measure and can be used by anyone for network reconnaissance, including hackers. However, the information collected from spam traps can be useful for identifying and preventing spam and other cyber threats.
Spam Trap
Spam traps are tools used by internet service providers to help manage fraud and block spammers, thereby making user inboxes safer. These traps create fake email addresses that are then used as bait for spammers. Legitimate emails sent to these addresses will often end up in the spam folder.
There are several different types of spam traps. One type is the username typo trap, which detects errors in email addresses that can be made by either humans or machines. Misspelled email addresses are a common trigger for this type of trap.
Another type of spam trap involves using expired email accounts. Some providers may use abandoned email accounts that are still associated with a domain name, which can then be used as spam traps.
Finally, some spammers may purchase email lists containing many invalid email addresses, which can trigger a spam trap. Since the sender does not have authorization to send emails to these addresses, they may end up on a blacklist and be treated as spammers.
Spam traps are an important tool for ISPs to help manage spam and keep users safe. By detecting and blocking spammers, they can help ensure that only legitimate emails end up in user inboxes.
Benefits of Honeypots
Simply deploying a honeypot in your network is not enough to ensure comprehensive security. There are several other security controls available, including intrusion detection systems, firewalls, intrusion prevention systems, and more, that you should consider implementing. The benefits of honeypots are described below:
- Distracts cybercriminals: A honeypot can distract cybercriminals and prevent them from targeting legitimate systems. The more time they spend on the honeypot, the less resources they have to target other parts of your network.
- Provides visibility: Honeypots allow for quick detection of attacks. The moment an attacker sends a keystroke, instant alerts are triggered and you get an opportunity to respond quickly.
- Monitors attacker behavior: Honeypots can be used to monitor attacker behavior and identify vulnerabilities. You can use published signatures to identify the type of attack being carried out.
- Tests incident response capabilities: Honeypots can be used to test your organization’s incident response capabilities. By preparing your team to take appropriate countermeasures, you can effectively block attackers and prevent them from accessing your network.
- Improves overall security: Honeypots can help improve your company’s overall security by shedding light on attackers and helping you develop effective prevention strategies.
- Cost-effective: Honeypots are a cost-effective method of enhancing network security. They only interact when malicious activity occurs and do not require high-performance resources to control network traffic during an attack.
- Captures all types of malicious activity: Honeypots can capture all types of malicious activity, including those that are encrypted.
- Collects valuable data: Honeypots collect data from attacks, including unauthorized activity and other useful information that can be used to improve your security posture.
While honeypots are a useful tool in enhancing network security, they should be used in conjunction with other security controls to ensure comprehensive protection against cyber threats.
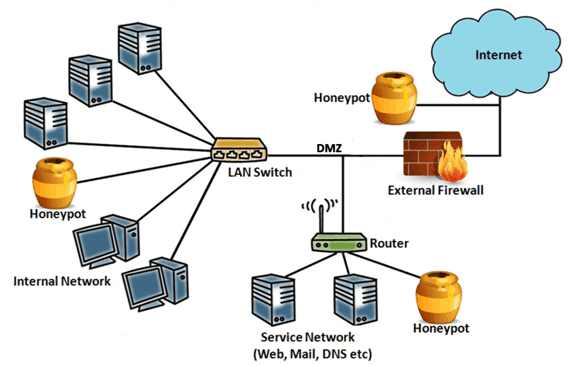
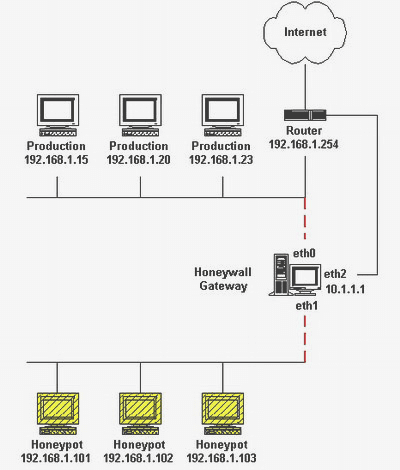
Honeynet
This honeynet includes two or more honeypots for one network. When you will have an interconnected network that time honeypot gets used. It allows the organization to track the attacker’s interaction with the resource.
It also helps you monitor intruder moves in the network so that you can interact with multiple points at one time. The main goal is to catch the hacker and successfully breach the network, so if you have more network destinations, it can be more convincing for the attacker.
Deception technology is the more complex implementation for the honeypots as well as a honeynet. It often packages with other technology like next-generation firewalls, Secure web gateways, and IDSes. This technology includes automated features where the honeypot can respond the real-time to potential attackers.
A network made up of two or more honeypots is called a honeynet. Having a connected honeypot network has certain advantages. Businesses can monitor how an intruder interacts with a single resource or network point, moves across points on the network, and interacts with many points simultaneously.
In order to increase the realism of the setup, it is intended to convince hackers that they have successfully penetrated the network. Deception technology refers to honeypots and honeynets with more sophisticated implementations, such as next-generation firewalls, intrusion detection systems (IDSes), and secure web gateways. ystem or piece of software known as an intrusion detection system keeps an eye out for malicious activity or network policy violations. A honeypot can react to potential attackers in real-time thanks to automated deception technology capabilities.
Honeypot can help businesses stay on top of the constantly shifting risk environment as new cyber threats appear. Even though it is hard to predict and stop every assault, honeypots provide essential information to make sure an organization is ready and are arguably the greatest way to catch an attacker in the act. They’re also a useful resource for experts in cybersecurity.
Conclusion
The implementation of a honeypot can aid organizations in mitigating the risks posed by an ever-evolving threat landscape. While predicting attacks is nearly impossible, honeypots can aid in the prevention of various attacks.
Honeypots are invaluable sources of information that ensure organizations are well-equipped to react in the event of an attacker’s actions. Cybersecurity professionals can rely on honeypots to obtain crucial hacking-related information.
Honeypots are an essential tool for organizations that prioritize their cybersecurity, as they can provide early warnings of potential attacks, and allow for the gathering of vital intelligence that can be used to prevent future attacks.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.
Join us to keep track of news: https://linktr.ee/coincu
Annie
Coincu News
0
0
 한 곳에서 모든 암호화폐, NFT 및 DeFi 를 관리하세요
한 곳에서 모든 암호화폐, NFT 및 DeFi 를 관리하세요시작하는 데 사용하는 포트폴리오를 안전하게 연결하세요.