Professional Sandwich Artist Rinses Crushed Trader For $700K In Onchain Heist
0
0

A crypto trader recently fell victim to a sophisticated on-chain heist attack, swapping $733,000 worth of USDC for $19,000 USDT in return. This incident shows the trading systems’ technical vulnerabilities and the cunning strategies employed by the crypto sandwich artist. The artist used precise timing and transaction ordering to drain the trader’s funds.
By taking advantage of the mechanics of automated market makers (AMMs) and the transparency of blockchain transactions, the attacker executed a heist that left the trader with a fraction of their original buy.
When a trader submits a large swap order, the transaction enters the Ethereum mempool, a public holding area for pending transactions. Miners or validators then pick up these transactions to include in the next block.
Because the blockchain is transparent, anyone can observe these pending trades, including the exact amount and token pair involved.
Since, in this case, the trader intended to swap a significant sum, the attacker sniped the victim’s large order and attacked the trade’s outcome.
Crypto trader swaps $733,000 for just $19,000 in large sandwich attack. pic.twitter.com/8gvF3zsZDY
— Sneta Gupta (@SnetaGupta) March 13, 2025
Sandwich Artist and His Crypto Heist: an On-Chain Lesson
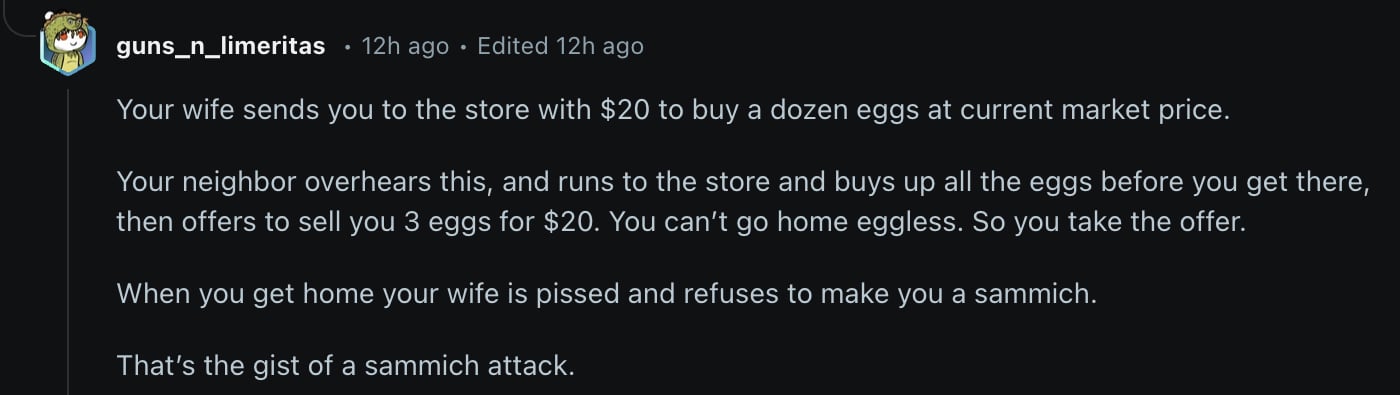
The crypto heist attack unfolded in two key steps. First, the sandwich artist placed a “frontrun” transaction ahead of the victim’s swap. This initial trade artificially inflated the token price the victim bought, driving up slippage (the difference between the expected price and the actual execution price).
Slippage is a common risk in large trades on AMMs, where liquidity pools can shift dramatically with big orders. The attacker ensured the victim would receive far fewer tokens than anticipated by pushing the price higher.
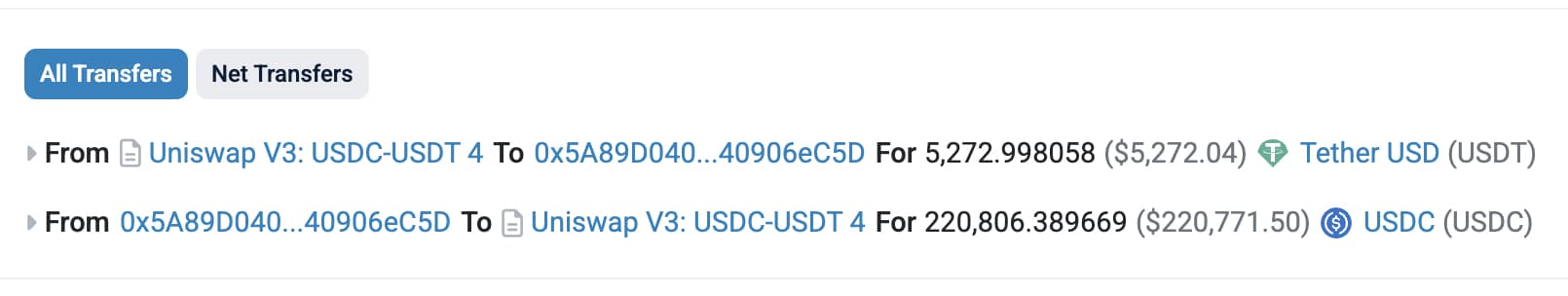
Then, after the victim’s trade executed, the attacker placed a second “backrun” transaction to sell the tokens they had just acquired at the inflated price, pocketing the difference. The result: the trader swapped $733,000 USDC for just $19,000 USDT, while the attacker walked away with $714,000 in profit.
This loss is recorded in 6 TXs, with one TX losing him more than $200,000.
(source)
Onchain data reveals the precision of this maneuver. The victim’s transaction was likely high enough to handle a typical trade but insufficient to absorb a massive order without significant price impact. The attack takes advantage of this crypto vulnerability and crafts its transactions to sandwich the victim’s order within the same block.
block time, averaging around 12-15 seconds gave the sandwich artist a narrow but sufficient window to execute both trades. The $19,000 return reflects the extreme slippage and the attacker’s ability to drain nearly all the value from the swap, leaving the trader with a tiny fraction of their purchase.DISCOVER: Best Meme Coin ICOs to Invest in March 2025
Discussing The Crypto Sandwich Attack: How to Avoid it
Is this practice illegal? Sandwich attacks exploit the open nature of crypto systems rather than hacking or stealing private keys, placing them in a gray area.
Some argue they’re fair game in the Wild West of crypto. Others see them as predatory, exploiting traders who don’t understand the intricacies of mempool dynamics or AMM pricing.
(source)
In this case, the trader’s loss was staggering, but no evidence suggests they were specifically targeted beyond being a large player in the wrong place at the wrong time.
Sandwich attacks aren’t new, but their profitability has increased as trading volumes on AMMs increase. Attackers often deploy bots to automate the process, scanning for large trades and executing the frontrun-backrun combo with minimal human intervention.
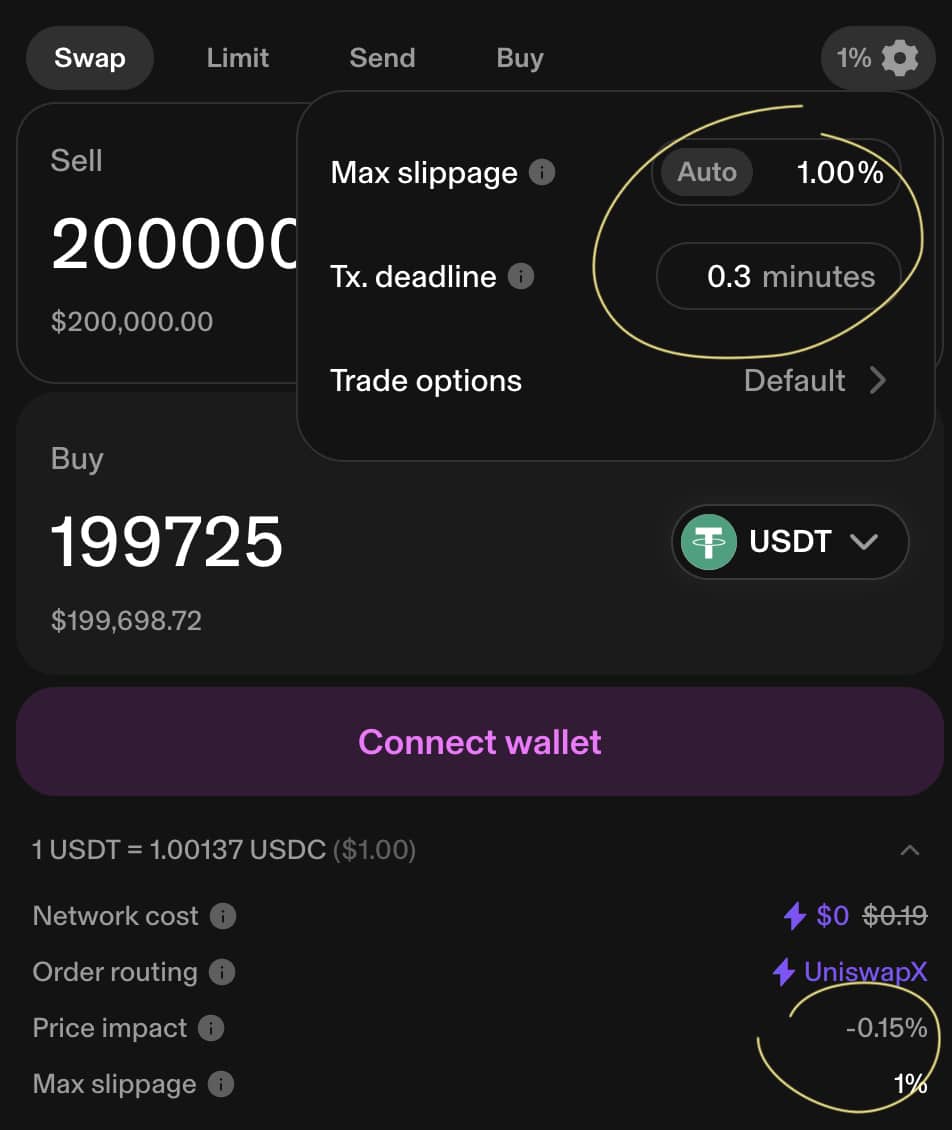
Mitigating such attacks is challenging but possible. Traders can use lower slippage tolerances, though this risks transaction failure if prices fluctuate too fast. Alternatively, submitting trades through private mempools or relay services can obscure them from prying eyes, though this often incurs higher fees.
(source)
Some DeFi platforms are exploring built-in protections, like dynamic slippage adjustments or anti-frontrunning mechanisms, but these remain in the early stages. For now, the burden falls on traders understanding the risks and adapting their strategies. Traders can trade safely by breaking large orders into smaller chunks or timing trades during lower network activity.
As the space evolves, so too will the cat-and-mouse game between traders and those who prey on their moves, with each heist refining the playbook for both sides.
DISCOVER: Avoid Crypto Heist with Anti-Sandwich Wallet
Join The 99Bitcoins News Discord Here For The Latest Market Updates
Key Takeaways
- The sandwich attack’s curve, a lesson to learn.
- How to avoid sandwich artist heist attack.
The post Professional Sandwich Artist Rinses Crushed Trader For $700K In Onchain Heist appeared first on 99Bitcoins.
0
0
 Manage all your crypto, NFT and DeFi from one place
Manage all your crypto, NFT and DeFi from one placeSecurely connect the portfolio you’re using to start.








