Monero Goes 36 Hours Safe After Qubic Selfish Mining Attacks
0
0
Monero, the leading privacy-focused cryptocurrency, has gone 36 hours safe from another selfish mining attack by the Qubic pool. Selfish mining is a strategy often seen as malicious that occurs when a miner, with a significant share of the network’s hashrate, intentionally delays broadcasting their mined blocks, causing a chain reorganization (reorg) or fork, invalidating other miners’ blocks and rewards.
On August 12, the Qubic Pool successfully caused a six-block chain reorg from block height 3,475,995 to 3,476,000, effectively rewriting this piece of Monero’s blockchain history and causing disruption. Many exchanges and services reportedly halted Monero XMR $258.2 24h volatility: 2.2% Market cap: $4.76 B Vol. 24h: $61.70 M deposits and withdrawals in response to what was wrongly called a 51% attack during the mining wars.
As of this writing, at block height 3,477,070, the blockchain registers zero orphaned blocks in the last 720 blocks (24 hours). “Orphan” is the name given to blocks that were replaced by a selfish miner during a chain reorg. There were 60 orphan blocks registered in the last 24 hours of Qubic’s attack on August 12, according to data from moneroconsensus.info.
Moreover, with 1,070 blocks confirmed after the six-block reorg without another similar event, Monero nears 36 hours safe from the attacks.
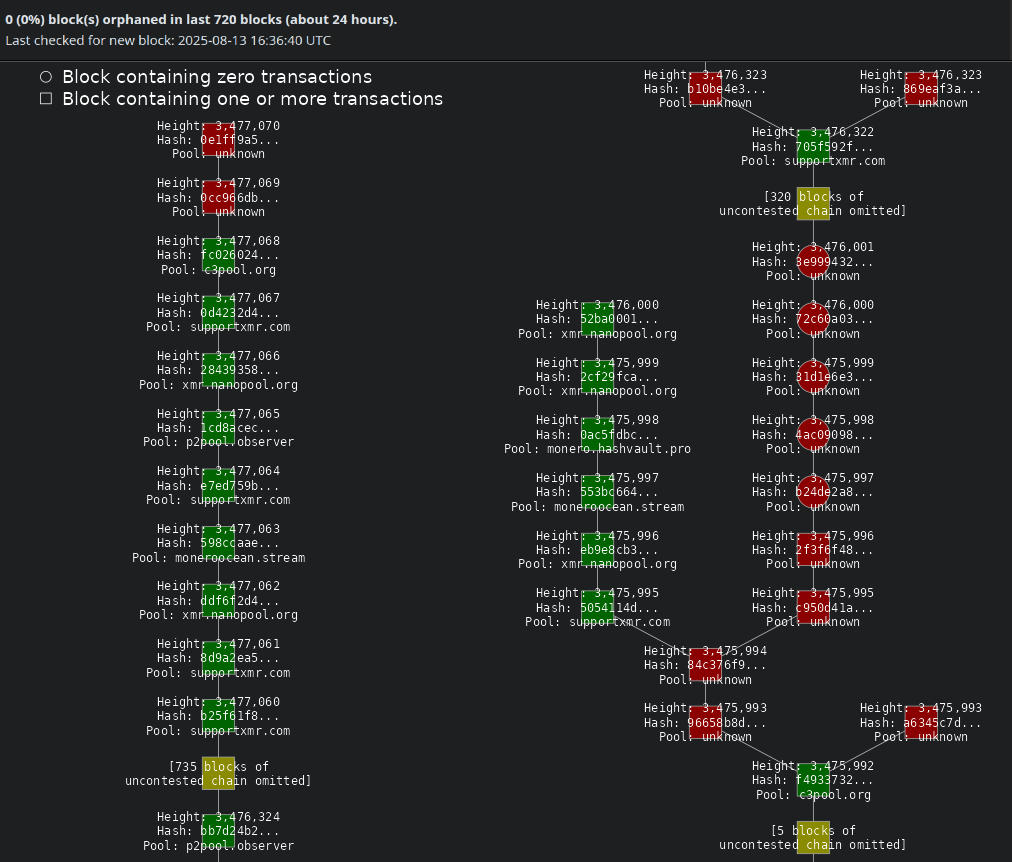
Monero Blockchain and Orphan Blocks Visualization | Source: moneroconsensus.info
Has Monero Suffered a 51% Attack by Qubic?
Most headlines regarding the six-block reorg from August 12 called the event a 51% attack against Monero, but this is a technical inaccuracy. A 51% attack, by definition, would require the attacker to control 51% or more of the network’s hashrate—while there is no evidence that it occurred in this case.
Luke Parker, a core developer and active contributor to Monero, explained in different commentaries on X that August 12’s event would have been possible with less than 51% of the hashrate, requiring the attacker to be “lucky.” Still, he notes that a significant amount of hashrate was still needed for that.
A 6 re-org does not mean a '51% attack' was successful. In that case, we'd see unbounded-depth re-orgs/no blocks mined by any other mining pool (assuming the adversary censors other mining pools, as this one does).
It does mean an adversary with a high amount of hash got lucky.
— Luke Parker (@kayabaNerve) August 12, 2025
A Qubic report of what was called the “Q Marathon” shows the pool successfully mined 251 out of 699 blocks in the 24 hours of the attack. This results in an approximate hashrate of 35.91%, slightly above one-third of the network and significantly lower than the claimed 51%.
~36% fyi
In other words, they are now profitably selfish mining.
Not a 51% attack. They are doing great at marketing though.https://t.co/pRtWqNITto pic.twitter.com/kLHbXrahXi
— ᴜɴᴛʀᴀᴄᴇᴀʙʟᴇ (@DontTraceMeBruh) August 12, 2025
Self-reported hashrate is not a trusted source, as it can be tampered with via network telemetry techniques. Measuring the true hashrate is a nearly impossible job because proof-of-work is a probabilistic science, requiring large samples of mined blocks for conclusive data. However, by the time the larger sample comes, the hashrate percentage could have already changed as many factors influence the share of each miner.
Additionally, as Luke Parker explained, a 51% attack would be able to repeat the selfish mining strategy over and over again, increasing the damage caused, allowing for double spends, censoring transactions by consistently mining empty blocks, and increasing the profit of the selfish miner with complete domination over the mining rewards.
Nevertheless, it remains a sensitive situation for the Monero network, services, users, and honest mining pools. With over 33% of the hashrate, a selfish mining strategy can be performed profitably, and further deep chain reorganizations might happen again. Experts recommend exchanges, services, and users wait for at least 10 block confirmations before deeming a transaction probabilistically secure, but even more could be needed depending on how things develop.
The post Monero Goes 36 Hours Safe After Qubic Selfish Mining Attacks appeared first on Coinspeaker.
0
0
 Manage all your crypto, NFT and DeFi from one place
Manage all your crypto, NFT and DeFi from one placeSecurely connect the portfolio you’re using to start.






