If You Got This Email From CoinTelegraph or Token Terminal, You Probably Got Scammed
0
0

In a sophisticated email phishing operation, scammers impersonating well-known cryptocurrency brands, including CoinTelegraph and Token Terminal, have swindled nearly $600,000 from unsuspecting victims.
The scammers utilized fake airdrop campaigns to lure users into a trap, culminating in a significant financial heist.
Email Scams Hide Behind Renowned Crypto Brands
ZachXBT, a pseudonymous on-chain detective, revealed that in less than 10 hours, the scam amassed close to $600,000. Shortly after, blockchain analytics firm Nansen reported that the fraudsters transferred approximately $520,000 in Ethereum (ETH) to Railgun’s mixer. This suggests an effort to hide the source of the funds.
Phishing scams involving criminals mimicking reputable companies to extract personal information were at the heart of this operation. The perpetrators sent emails masquerading as communications from CoinTelegraph, Token Terminal, Wallet Connect, and De.Fi. This tactic allowed them to deceive users convincingly.
Read more: Who Is ZachXBT, the Crypto Sleuth Exposing Scams?
Nansen’s analysis disclosed that over $85,000 remained in the address where the stolen funds were initially deposited, spread across roughly 280 different tokens.
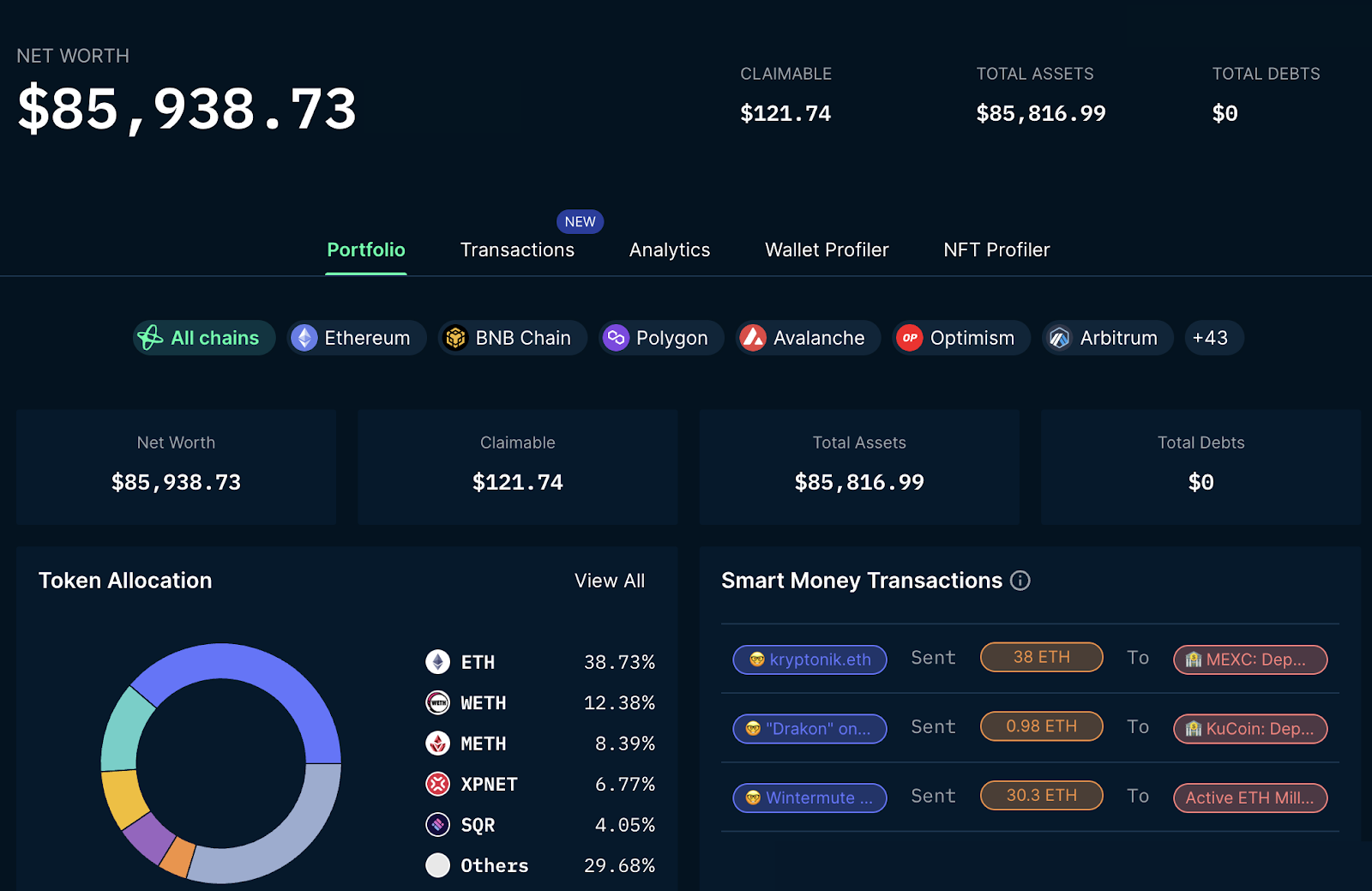 Net Worth of Email Scammers. Source: Nansen
Net Worth of Email Scammers. Source: Nansen
This incident follows the JITO token airdrop that excited the crypto community, with average payouts of $10,000 to early adopters using Solana’s liquid staking protocol. The scam capitalized on the heightened interest in airdrops, with all phishing emails promoting similar fraudulent schemes.
The scammers orchestrated phishing attacks through MailerLite, an email service provider targeting the crypto market. The breach occurred after a support team member inadvertently provided the attackers access to MailerLite’s internal system. The attackers reset passwords, gained unauthorized control, and focused specifically on cryptocurrency-related accounts.
MailerLite reported that 117 accounts were compromised, with a few used to launch additional phishing campaigns.
“Upon gaining access, the perpetrators executed a password reset for a specific user on the admin panel, further consolidating their unauthorized control. With this level of access, they were able to impersonate user accounts. The focus was exclusively on cryptocurrency-related accounts.” Mailerlite said.
Read more: 15 Most Common Crypto Scams To Look Out For
Following the breach, MailerLite has resolved the issue, terminated the access method used by the hackers, and pledged to enhance its internal processes and security training.
0
0









